General VanHerck joined D-Fend’s Advisory Board in October 2025. General VanHerck retired from the U.S. Air Force in 2024 after a distinguished career, culminating as Commander of U.S. Northern Command (USNORTHCOM) and North American Aerospace Defense Command (NORAD), where he oversaw the defense of North America, including critical infrastructure and homeland security. He previously served as Director of the Joint Staff at the Pentagon and Commander of the USAF Warfare Center at Nellis AFB, NV.
The use of unmanned airborne systems, including drones, is evolving rapidly. These systems, many of which are publicly available, are transforming society through responsible and beneficial use, while simultaneously, rogue actors, utilizing unmanned systems, present a multitude of threats, ranging from surveillance and espionage to weaponized attacks on critical infrastructure, such as the recent Spiders Web attack in Russia which caused significant damage to Russia’s strategic bomber fleet. Effectively countering unmanned systems requires key policy decisions and a cost-effective, flexible, and rapidly adaptable software driven layered defense solution.
A layered approach
A single solution or capability, call it a silver bullet, does not exist. In other words, no single capability will reliably deny or defeat unmanned systems, in every situation. Many threat systems utilize radio linked technology and respond predictably to electronic countermeasures. Others are fully autonomous, highly hardened with low radar signature, and/or non-emitting (“dark”), ignoring electronic interventions. These varying characteristics demand an approach which layers multiple technologies and capabilities, relying on different physical attributes where the various layers cover the limitations of another, resulting in more resilient detection and mitigation, fewer false alarms, and a clear escalation path. This approach also supports sequentially introducing capabilities as needed to counter a changing environment, and to address the vast majority of threats in a cost-effective manner.
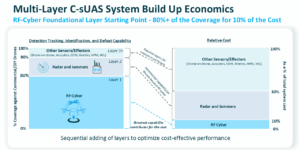
To be effective, and just as important, efficient, a layered architecture must have the following attributes. Sensor and effector capabilities to address the anticipated threats in the operational area. Cost per effect must be affordable, while also ensuring effector capacity to deny or defeat potentially large quantities of threats. Third, to remain viable long term and in today’s dynamic environment, it must be software-defined and rapidly adaptable, allowing for updates and programming while fielded. Finally, it must operate in our national airspace, in close proximity to the public, including commercial and general aviation aircraft, with no and low collateral damage options. The attributes point to a layered system with a foundational layer defined by RF-Cyber sensing and effects with optional optics for visual detection. Additional layered capabilities could include smart jamming as a mitigation backup and for vital critical infrastructure, kinetic capabilities and systems such as lasers or high-powered microwave.
RF-Cyber, for both sensing and effects, is ideal for four operational reasons: effectiveness, safety, control, and continuity. Effectiveness: Field experience from around the globe shows that a vast majority (>80%) of drones encountered are Commercial and based on publicly available technology and can be dealt with using RF-Cyber techniques. Safety: RF-Cyber sensing and effects do not create falling debris or blast fragments thus greatly reducing the risk of collateral damage. Control: RF-Cyber enables operators to assume command of a hostile platform and trigger a managed, safe route landing sequence, preserving forensic evidence and enabling the user to determine where the drone will come down. Continuity: RF-Cyber avoids broad spectrum disruption, so friendly communications, sensors, and mission systems continue to operate without interruption. RF-Cyber’s ability to surgically deny or defeat the threat makes this capability the logical foundation for any layered counter drone/UAS system, military or commercial.
Subsequent Layers: Radar, Jamming, Optics, and Exotic Capabilities
Where detection and defeat coverage approaching 100% is required, the next logical layer to add to RF-Cyber is radar for detection and jamming for defeat. Working together, RF-Cyber and radar cover the bulk of common commercial and publicly available UAS platforms. By fusing RF-Cyber, radar, optional optics and jamming, the resulting C-UAS solution addresses most relevant drone types, keeps cost to defeat low, and remains adaptable over time. This combination yields a practical, low-collateral, and sustainable defense posture suitable for protecting military installations, borders, and critical infrastructure. Beyond this, for crucial critical infrastructure, where a higher risk is involved and where 100% defeat coverage may be required, more expensive and exotic capabilities can be added including kinetic, high-power microwave and laser weapons.
Other Considerations: Cost per defeat, Software-based for future-proofing
Cost to defeat is the marginal expense of neutralizing a single drone. It includes expendables, energy, and operational overhead directly tied to an engagement. RF-Cyber and the marginal energy for a short, directed energy pulse can be inexpensive. Interceptor drones and net-capture systems fall into a middle cost band. At the high end there are missiles, which can cost tens or hundreds of thousands of dollars per engagement. In sustained operations or swarm scenarios, cost to defeat may determine duration of defense posture and overall magazine depth. A cost-effective design therefore attempts the least expensive effective mitigation first and escalates only when necessary. Because RF-Cyber and jamming are primarily software and energy effects, their marginal cost per engagement is effectively near zero. That contrasts directly with expendable interceptors that cost tens or hundreds of thousands of dollars each. As a result, the fused system sustains defensive coverage for longer periods and at lower cost than architectures that rely on kinetic effectors.
The figure below depicts the sequential layering described in this paper in terms of both coverage and cost.
A software-first architecture enables rapid adaptation. Knowledge bases, libraries, and machine learning classifiers allow operators to update detection and mitigation rules as new drone models and RF behaviors appear. Remote updates, built-in test modes, and a validation pipeline from lab to field ensure changes are safe and effective. Because the core effects are software-driven rather than hardware-replacement driven, the system stays effective as adversaries evolve, and new threats emerge.
Closing thoughts
For leaders responsible for protecting military installations, national borders and critical infrastructure, both military and commercial, from drone incursions the operational prescription is clear. Detect and defeat the threat by deploying a layered system with RF-cyber as its foundation. As required, and directed by policy and priority, build on this foundation adding sensing and defeat capabilities such as radar, jammers, kinetics and exotic technologies, as required. This approach allows for cost effective implementation and execution, reduces risk from collateral damage, increases system capacity and magazine depth, and preserves continuity of operations, services, and communications.